Security Virtual Keyboards: Why you should avoid using them
Virtual keyboards are popup keyboards that allow you to
enter text into a form. These keyboards appear on the screen and allow you to
type in text. On devices such as smartphones in which maximising the viewable
screen is crucial, virtual keyboards are ideal because they appear only when
they are required. After they are done with they disappear, returning the area
they occupied back to the user. In those environments in which miniaturization
is not so important, physical keyboards are normally the preferred device to
enter text into an application although many computers support virtual
keyboards to cater for those instances when a keyboard is not available.
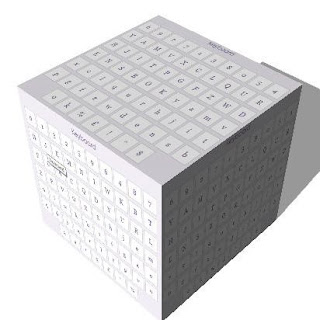
Security Virtual Keyboards (SVKs) have evolved from the
standard virtual keyboard and are marketed by organizations that sell or use
them as tools that enhance security. These keyboards are normally associated
with particular text boxes in a form and will automatically pop up when the
person filling the form lands on the text box associated with the SVK.
SVKs are similar to standard virtual keyboards in that both
are not physical. They normally differ in that:
●
The layout of the keys changes each time the SVK
pops up;
●
They disable input through a physical keyboard
even when a physical keyboard is present;
●
What is typed is not shown in the text box (as
is the case with password fields).
While they are usually associated with password fields there
are organizations that go wild and fire up SVKs with other inputs such as
usernames.
SVKs are a bad idea and any security-conscious organization
should avoid using them.
- Fact: SVKs make
use of a pointing arrow (or finger)
In crowded environments such as
offices and client-facing environments, observing the position of a moving
white arrow or an index finger on a laptop touch screen is easier than
observing the letters being punched in with a keyboard.
Source:
https://www.pexels.com/photo/business-businessmen-classroom-communication-267507/
- Fact: SVKs slow
users down.
Since the layout of the keys
constantly changes users need to constantly reorientation themselves on where
the keys are. This considerably slows down the user thereby making it easier
for an onlooker to read what is being entered.
- Fact: SVKs
advertise themselves to casual hackers.
In an office full of keyboards
hearing the tapping of fingers on keys is an expected event. No one’s attention
would be alerted. On the other hand, a keyboard-on-the-screen is not a common
occurrence and a casual onlooker might be tempted to “discover more”.
- Fallacy: SVKs
make it difficult for key loggers to grab a password.
Key loggers constitute the
simplest and most basic method of eavesdropping. Today software that allows
content to be captured go beyond simply reading the keyboard stream; they
capture screens as well as all mouse actions thereby allowing SVKs to be
circumvented. So the act of simply
moving keys around on a desktop will not circumvent malware that monitors such
activity.
In the networked world we live in,
most unauthorised eavesdropping has evolved beyond screens, they intercept the
stream of communications between the device by tapping into the communication
stream between the source of the communication (the user) and the destination
(the place the user wants to interact with) or by pretending to be the
destination (phishing).
Companies that market SVKs have
a commercial intention of convincing us that their product enhances security
and some of us take their advertising claims as factual. We need to challenge
marketing statements so as to avoid a false sense of security.
Security is a dynamic topic that
evolves. Even if something was an effective security tool in the past, changing
technologies and how we work could not only make the tool ineffective but could
be abused by hackers. One needs to constantly be on the alert.


Comments
Post a Comment